Видео с ютуба What Are Rsa Vulnerabilities

Breaking RSA - Computerphile
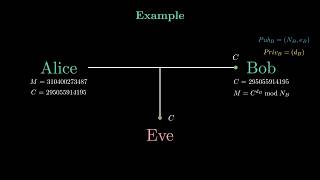
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

Some Attacks Against RSA

RSA 2023: Ben Edwards & Sander Vinberg - Evolution of CVEs and Vulnerability Management

Anatomy of the RSA targeted attack

ECED4406 0x20A - RSA Attacks

Introduction to Cryptography: Security of RSA

Between Two Vulns: RSA Special - Fun Times and Critical Vulnerabilities

Quantum Researchers Break RSA Encryption

AI Security Engineering—Modeling/Detecting/Mitigating New Vulnerabilities

What is RSA?

Attacks on RSA || Lesson 61 || Cryptography || Learning Monkey ||

DROWN Attack - Decrypting RSA using Obsolete and Weakened eNcryption (TLS Academy)

RSA Security Analytics Demo

Quantum Attacks: Are Your Encryption Algorithms Safe? (RSA, ECC, AES)

Quantum Attack: RSA & ECC Cryptography's Biggest Threat?

RSA® Conference 2011 -- Top Website Vulnerabilities: Trends, Business Effects and How to Fight Them

ROCA: Vulnerable RSA key generation | Petr Švenda

RSA Certificate | RSA Certificate Explained